Datto Endpoint Detection and
Response Software (EDR)
EFFORTLESS & EFFECTIVE
Remote Data Backups is a Datto Distributor and a Kaseya 365 Distributor.
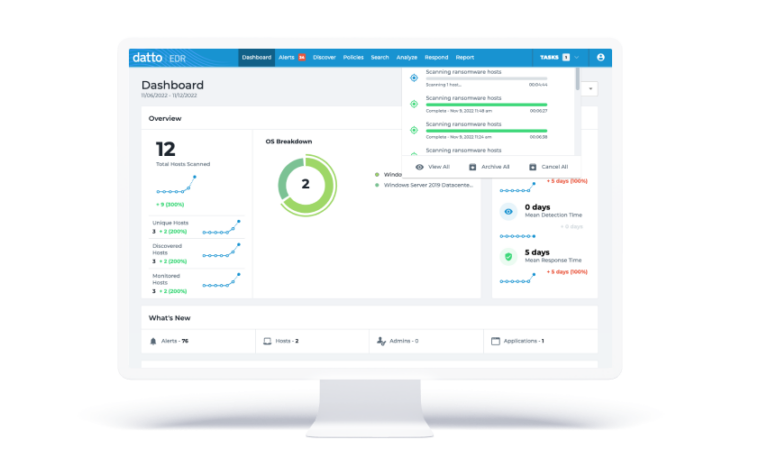
With Datto Endpoint Detection and Response (EDR) you can detect and respond to advanced threats. Datto EDR is an easy to use cloud based EDR solution that’s designed for your business.
Proven Efficacy Against Advanced Threats
Datto EDR is independently verified and proven as a leader against malware and advanced threats. Miercom, a global leader in cybersecurity testing, found that Datto EDR detects and stops 99.62% of all malware when combined with Datto AV.
Easily Stop Zero Day Threats
With new threats being developed and released into the wild every day, rest assured knowing that even the most advanced threats are caught by Datto EDR.
Eliminate Alert Fatigue
You don’t have to be a security expert to get security expertise. Datto EDR Smart Recommendations eliminate alert fatigue, while the correlation engine reduces unnecessary noise. Empowering you to focus on what matters most.
Easy Management and Response
Seamless integration with Datto RMM allows one-click EDR deployment, alert response, device isolation, and dashboard access. This reduces product switching, streamlining management, response and visibility, saving you precious time.
Comprehensive Advanced Threat Protection
Experience robust cybersecurity with Datto AV, Datto EDR, and Datto Managed SOC, powered by RocketCyber. This integrated solution ensures antivirus protection, continuous endpoint monitoring, and 24/7 expert managed detection and response.
Key Datto EDR capabilities
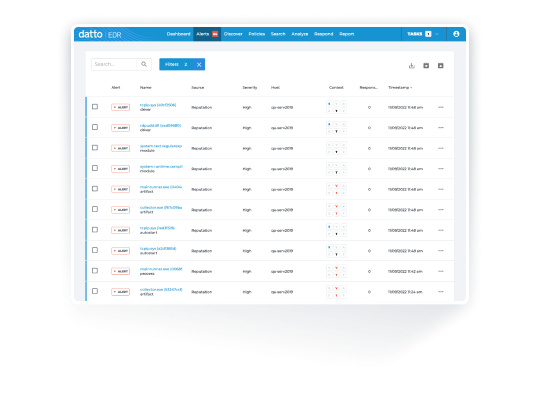
Sophisticated threat detection and response: Datto EDR detects threats and suspicious behaviors that evade other defenses so that you can quickly respond before damage is done.
Click-to-respond
Take action against advanced threats right from your alert dashboard. Isolate hosts, terminate processes, delete files, and more without wasting precious seconds with our scalable remote response actions.
Detect Fileless Attacks
Eliminate even the most elusive threats that traditional antiviruses will not catch with Datto EDR’s patented deep memory analysis to ensure suspicious behaviors and advanced threats are detected.
MITRE ATT&CK mapping
Our alerts are mapped to the MITRE ATT&CK framework to provide context and helpful clarity to your team, reducing the security expertise required to effectively respond.
Smart Recommendations
Our seasoned SOC analysts have distilled their experience into building automated mitigation recommendations for today’s advanced threats.
Advanced Correlation Engine
Datto EDR boasts a patented correlation engine which reduces unnecessary noise allowing IT professionals to focus on real threats and not drown in false positives.
Automated Threat Response
Interrupt the kill chain with 65+ automated threat responses to isolate hosts, kill processes, or quarantine files without the need of complicated scripting knowledge.
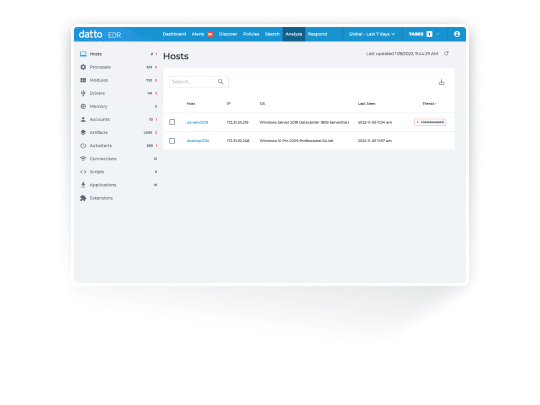
Multi-platform Support
Datto EDR defends all endpoints: desktops, notebooks and servers, across Windows, MacOS and Linux operating systems.
Now, more than ever you need advanced threat protection across all of your endpoints. Datto EDR eliminates traditional EDR headaches, making endpoint detection and response easy to deploy, manage and use.
Commonly Asked Questions about EDR Solutions
What is endpoint detection and response software?
Endpoint Detection and Response (EDR) is an endpoint security solution or software that continuously monitors end-user devices (Laptops, desktop, tablets, etc.) to detect and respond to cyber threats such ransomware and malware.
Endpoint Detection and Response can sometimes be referred to as endpoint detection and threat response (EDTR).
Due to endpoint detection and response technical nature its normally managed by an IT Service provider or Managed Service Provider (MSPs)
When it comes to choosing the correct EDR tool it’s essential to know what you are looking to prevent and the scale of the threats that you and your end users are facing.
5 tips for choosing an endpoint security solution
Cyber-attack Prevention, Continuous Monitoring and Recording, Rapid breach Detection, Automated Response, & Integrated Threat Defense ensure a better protected environment.
Yes, antivirus is considered as the minimum security standard. Endpoint detection and response tools are an additional grade of security to deal with advanced threats that are not normally detected by AV tools.
Endpoint Detection and Response (EDR) includes advanced capabilities like detecting and investigating security incidents, and ability to remediate endpoints to pre-infection state. However Endpoint Protection Platform (EPP) covers traditional anti-malware scanning.
Endpoint Detection and Response (EDR) is defined as a set of cybersecurity tools which are designed to detect and respond to any malware or any other form of malicious activity on an endpoint.
Endpoint Detection and Response (EDR) is an integrated, layered approach to endpoint protection that combines real-time continuous monitoring and endpoint data analytics with rule-based automated response.
EDR + MANAGED SOC (MDR)
IS A GAME-CHANGER
Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR), also known as Managed SOC (security operations center), are powerhouse security technologies. While each is an excellent solution on its own, the real magic lies in using them in concert to gain a big security advantage. It’s a game-changer that gives companies an array of benefits including 360 visibility into their threat picture, valuable threat intelligence and critical tools to speed incident response.
Aren’t EDR and MDR the same thing?
EDR and MDR may have similar abbreviations, but they’re
not the same technology. Instead, each provides IT teams
with part of a company’s threat picture.
EDR focuses on detecting and responding to threats
at the endpoint level, such as laptops, servers, and
other computing devices. It uses advanced techniques
such as behavioral analysis, machine learning, and
threat intelligence to detect and respond to threats that
traditional antivirus solutions may miss.
Managed SOC or MDR is a comprehensive security
solution that involves a combination of people, processes,
and technology to detect, investigate, and respond to
security incidents across the entire organization. Managed
SOC services are typically provided by a third-party vendor
who monitors their customer’s network and endpoints for
suspicious activity.
EDR and Managed SOC – Better Together
The combination of EDR and Managed SOC together offers
an array of unbeatable benefits including:
1. Comprehensive Threat Detection: By combining
EDR and Managed SOC, an organization can achieve
comprehensive threat detection capabilities. EDR can
detect threats at the endpoint level, while Managed
SOC can detect threats across an entire organization’s
IT infrastructure, including cloud, networks, and
various endpoints, including servers, as well as
other devices.
2. Faster Incident Response: EDR can quickly detect
and respond to threats at the endpoint level, but
adding Managed SOC can provide even faster
incident response by quickly correlating threat data
from multiple sources and providing a holistic view of
the incident. This allows organizations to respond to
threats more quickly and effectively.
3. Improved Threat Intelligence: EDR can provide
valuable threat intelligence to Managed SOC
services, which can help them improve their detection
capabilities. For example, if EDR detects a new type of
malware, it can immediately send that information to
Managed SOC analysts, allowing them to update their
detection capabilities.
4. Reduced False Positives: EDR can help reduce the
number of false positives generated by Managed SOC
services by providing more context around alerts.
For example, if EDR detects a suspicious file on an
endpoint, it can provide additional information about
that file to the Managed SOC analysts, allowing them
to better determine whether it’s a true threat or a
false positive.
5. Reduced Tool and Vendor Fatigue: By leveraging a
joint EDR and Managed SOC solution, IT professionals
simplify their cybersecurity tool stack and reduce the
number of disparate security vendors that they must
use in order to stay secure. Not only does this save
time and money but makes the day-to-day workload
more efficient for the IT professional.
EDR and Managed SOC: The Perfect Match
EDR and Managed SOC are powerhouse technologies
that complement each other perfectly. This winning
combination can affordably provide organizations
with a better defense-in-depth posture. By combining
the two, MSPs can achieve faster incident response,
improved threat intelligence and reduce false positives
while minimizing tool and vendor fatigue, giving you
and your clients the security edge you need in today’s
dangerous world.
Datto EDR – Endpoint Detection Made Easy
Datto EDR empowers IT teams to detect and respond to
advanced threats quickly and efficiently. An easy-to-use
cloud based EDR solution that’s purpose built for Managed
Service Providers (MSPs), Datto EDR defends all endpoints:
desktops, notebooks and servers, across Windows, MacOS
and Linux operating systems and integrates seamlessly
with Managed SOC and Datto RMM.-
Patented deep memory analysis ensures that you’re
informed of even the most elusive threat actors.
Take action against advanced threats right from
your alert dashboard to isolate hosts, terminate
processes, delete files, and more without wasting
precious seconds.- Alerts are mapped to the MITRE ATT&CK framework
to provide context and helpful clarity to your team.
- Managed SOC powered by RocketCyber
Managed SOC is a white labeled managed service that
leverages our Threat Monitoring Platform to detect
malicious and suspicious activity across three critical
attack vectors: endpoint, network and cloud. Our elite team
of security veterans hunt, triage and work with your team
when actionable threats are discovered including:
Continuous Monitoring – Around the clock protection with
real-time threat detection.
World Class Security Stack – 100% purpose-built platform
backed by over 50 years of security experience.
Breach Detection – The most advanced detection with to
catch attacks that evade traditional defenses.
Threat Hunting – Elite security team proactively hunt for
malicious activity.- No Hardware Required – Patent pending cloud-based
technology eliminates the need for on-prem hardware.
Try it today!
Human Support
1 (866) 722-2587
Support Hours 24/7
Get Started
Let us answer your questions. Call now to speak to an expert or book an appointment today. Consultations are always free

Trust The Lighthouse
Datto Distributor & Kaseya 365 Distributor
A solution for every backup & recovery need.
Human Support
1 866 722 2587