Datto SOC Managed Detection Response Powered by RocketCyber
Managed Security Operation Center (SOC) for MSPs
Remote Data Backups is a Datto Distributor and a Kaseya 365 Distributor.
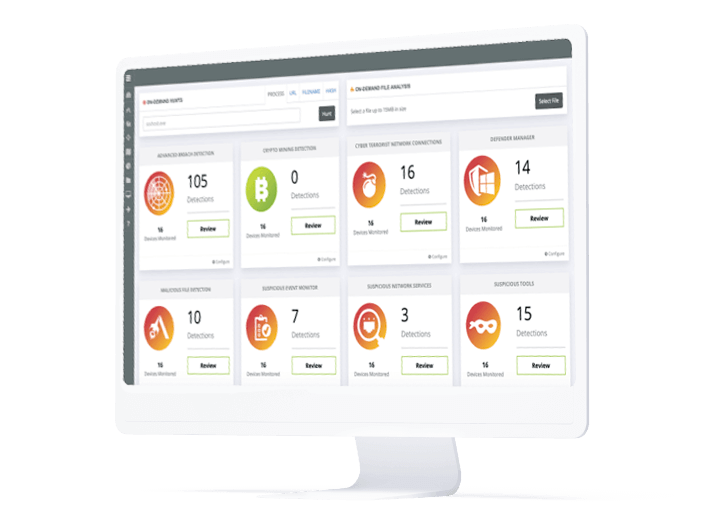
With Datto Managed SOC, (Managed Detection Response) powered by RocketCyber, managed service providers (MSPs) can stop cyberattacks in their tracks. Built-in 24/7 threat monitoring enables rapid detection and response of threats, backed by a world-class security operations center.
24/7 Security Managed by Cybersecurity Experts
Datto Managed SOC is a white labeled managed detection and response service. By leveraging RocketCyber’s Threat Monitoring Platform, Datto Managed SOC detects suspicious activity across endpoints, networks and cloud environments. Our team of cybersecurity veterans hunt, triage and work with your team when actionable threats are discovered.
Continuous monitoring
Datto Managed SOC’s real-time threat detection enables you and your clients to relax knowing you have around the clock protection.
World-class security stack
Our Managed SOC was purpose-built to provide world class service and is backed by over 50 years of cybersecurity experience.

Breach detection
Take your breach detection to the next level by detecting attacks that evade traditional cyber defenses.
Threat hunting
Respond to the latest threats with our elite security analyst team that proactively hunts for malicious activity and helps you respond.
Secure and Protect Clients with Managed SOC – No Hardware Required

Comprehensive Endpoint Security
Datto Managed SOC enables managed service providers to protect your Windows and MacOS endpoints. With built in advanced breach detection, event log monitoring and intrusion detection you can respond rapidly to an attack. We also include proactive threat hunting and integrations with 3rd party next-gen AV solutions to ensure a layered security approach.
Real Time Network Security
Gain new levels of network protection with Datto Managed SOC. With real time threat reputation and malicious connection alerts you can respond to network attacks quickly. Datto Managed SOC also includes log monitoring for firewall and edge devices as well as managing DNS information.
Cloud Security and Monitoring
Take your security detection and response best practices to the cloud. Datto Managed SOC enables you to monitor and respond to Microsoft 365 malicious activity. Datto Managed SOC also includes Microsoft 365 and Azure AD security event log monitoring and provides you with an overall Secure Score.
No Hardware Required
Datto Managed SOC deployment couldn’t be any easier, due to it being entirely cloud based. With no required hardware you can deploy Managed SOC with ease and reduce overhead by not maintaining expensive hardware.
Datto Managed SOC – Key Features
We save you time and money by leveraging your existing tools and cybersecurity investments across endpoint, network and cloud. This allows you to focus on what matters most – your business.
Threat Hunting and Intel
We take on the latest threats with real-time threat intelligence monitoring so you don’t have to. Pulling from multiple threat intelligence feeds, our SOC analysts utilize the largest global repository of real-time threat indicators to hunt down emerging threats.
Seamless Log Monitoring
Datto Managed SOC log monitoring enables you to monitor, detect and respond to changes across endpoints, networks and cloud infrastructures. Key log data is pulled from Windows and MacOS endpoints, network firewalls / edge devices and Microsoft 365 & Azure AD without requiring a SIEM or SIEM hardware.
Breach Detection
Datto Managed SOC identifies tactics, techniques and procedures used by attackers. It aligns these to MITRE ATT&CK, making breach detection and response effective, effortless and easy.
Integration with PSA ticketing
When a threat is detected our SOC analysts investigate and triage each incident. They then create detailed tickets for your PSA system – such as Autotask PSA. These tickets include remediation details so you can respond quickly without having to hire additional staff.
Next-Generation Malware Detection
Take your malware detection to the next level with a Datto Managed SOC.
As part of a multi-layered security approach you can use your preferred malware prevention or our Microsoft Defender command and control application. This includes malicious detection of files, tools, processes and more.
Intrusion Monitoring
Datto Managed SOC includes real-time intrusion monitoring to detect threats before they cause widespread damage.
By monitoring for suspicious activity, such as accessing unauthorized services and backdoor connections, you can be alerted before attacks succeed.
Additional Security with Key Integrations
Datto Managed SOC, powered by RocketCyber includes a wide range of additional security integrations via our App Store. These additional tools are all able to be monitored by our SOC analysts 24/7.
AV/ AM Monitoring
BitDefender
Cylance
Deep Instinct
SentinelOne
Sophos
Webroot
Windows Defender
Firewall Analyzer & Monitoring
Barracuda
Cisco Meraki
Fortinet
Juniper
PfSense
SonicWall
Sophos
Ubiquiti
Untangle
WatchGuard
Email Monitoring & DNS Monitoring
Barracuda
DNSFilter
IRONSCALES
Microsoft 365
EDR + MANAGED SOC (MDR)
IS A GAME-CHANGER
Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR), also known as Managed SOC (security operations center), are powerhouse security technologies. While each is an excellent solution on its own, the real magic lies in using them in concert to gain a big security advantage. It’s a game-changer that gives companies an array of benefits including 360 visibility into their threat picture, valuable threat intelligence and critical tools to speed incident response.
Aren’t EDR and MDR the same thing?
EDR and MDR may have similar abbreviations, but they’re
not the same technology. Instead, each provides IT teams
with part of a company’s threat picture.
EDR focuses on detecting and responding to threats
at the endpoint level, such as laptops, servers, and
other computing devices. It uses advanced techniques
such as behavioral analysis, machine learning, and
threat intelligence to detect and respond to threats that
traditional antivirus solutions may miss.
Managed SOC or MDR is a comprehensive security
solution that involves a combination of people, processes,
and technology to detect, investigate, and respond to
security incidents across the entire organization. Managed
SOC services are typically provided by a third-party vendor
who monitors their customer’s network and endpoints for
suspicious activity.
EDR and Managed SOC – Better Together
The combination of EDR and Managed SOC together offers
an array of unbeatable benefits including:
1. Comprehensive Threat Detection: By combining
EDR and Managed SOC, an organization can achieve
comprehensive threat detection capabilities. EDR can
detect threats at the endpoint level, while Managed
SOC can detect threats across an entire organization’s
IT infrastructure, including cloud, networks, and
various endpoints, including servers, as well as
other devices.
2. Faster Incident Response: EDR can quickly detect
and respond to threats at the endpoint level, but
adding Managed SOC can provide even faster
incident response by quickly correlating threat data
from multiple sources and providing a holistic view of
the incident. This allows organizations to respond to
threats more quickly and effectively.
3. Improved Threat Intelligence: EDR can provide
valuable threat intelligence to Managed SOC
services, which can help them improve their detection
capabilities. For example, if EDR detects a new type of
malware, it can immediately send that information to
Managed SOC analysts, allowing them to update their
detection capabilities.
4. Reduced False Positives: EDR can help reduce the
number of false positives generated by Managed SOC
services by providing more context around alerts.
For example, if EDR detects a suspicious file on an
endpoint, it can provide additional information about
that file to the Managed SOC analysts, allowing them
to better determine whether it’s a true threat or a
false positive.
5. Reduced Tool and Vendor Fatigue: By leveraging a
joint EDR and Managed SOC solution, IT professionals
simplify their cybersecurity tool stack and reduce the
number of disparate security vendors that they must
use in order to stay secure. Not only does this save
time and money but makes the day-to-day workload
more efficient for the IT professional.
EDR and Managed SOC: The Perfect Match
EDR and Managed SOC are powerhouse technologies
that complement each other perfectly. This winning
combination can affordably provide organizations
with a better defense-in-depth posture. By combining
the two, MSPs can achieve faster incident response,
improved threat intelligence and reduce false positives
while minimizing tool and vendor fatigue, giving you
and your clients the security edge you need in today’s
dangerous world.
Datto EDR – Endpoint Detection Made Easy
Datto EDR empowers IT teams to detect and respond to
advanced threats quickly and efficiently. An easy-to-use
cloud based EDR solution that’s purpose built for Managed
Service Providers (MSPs), Datto EDR defends all endpoints:
desktops, notebooks and servers, across Windows, MacOS
and Linux operating systems and integrates seamlessly
with Managed SOC and Datto RMM.-
Patented deep memory analysis ensures that you’re
informed of even the most elusive threat actors.
Take action against advanced threats right from
your alert dashboard to isolate hosts, terminate
processes, delete files, and more without wasting
precious seconds.- Alerts are mapped to the MITRE ATT&CK framework
to provide context and helpful clarity to your team.
- Managed SOC powered by RocketCyber
Managed SOC is a white labeled managed service that
leverages our Threat Monitoring Platform to detect
malicious and suspicious activity across three critical
attack vectors: endpoint, network and cloud. Our elite team
of security veterans hunt, triage and work with your team
when actionable threats are discovered including:
Continuous Monitoring – Around the clock protection with
real-time threat detection.
World Class Security Stack – 100% purpose-built platform
backed by over 50 years of security experience.
Breach Detection – The most advanced detection with to
catch attacks that evade traditional defenses.
Threat Hunting – Elite security team proactively hunt for
malicious activity.- No Hardware Required – Patent pending cloud-based
technology eliminates the need for on-prem hardware.
Trust The Lighthouse
Datto Distributor & Kaseya 365 Distributor
A solution for every backup & recovery need.
Human Support
1 866 722 2587


