Remote Data Backups is a 25-year Backup and Recovery Distributor with 24/7 U.S.-based support. Our affiliate program is 25 years strong. Partners receive an onboarding affiliate link to post within their content. This link allows RDBU affiliates to receive credit for new clients automatically. Our partners receive a 20% recurring income month after month. RDBU manages all clients and tech support. Reoccurring affiliate commission checks are directly deposited monthly. Backup and Recovery is our niche and area of expertise, and our partners built our business. Our service supports backups for PC’s, servers, SaaS, and virtual machines.
Learn More: Backup Blog
Knowing why image backups are rapidly replacing file and folder backups is critical to the health of your data.
The Truth About Bare Metal Backup vs. File and Folder Backup
By Amanda Finch | RDBU Marketing
Recently, image backup, also known as bare-metal recovery, has quickly become the preferred data protection method for PCs, servers, and virtual machines.
Today’s complex IT environments have forced users to adjust to new backup methods. File and folder backups have now become a more time-consuming process.
A challenge during the setup process of a new computer is trying to transfer one’s computer data from the prior PC. Another challenge is completing a full recovery. These are two areas where bare metal recovery (image backups) shines.
Top 5 reasons why image backups are replacing file and folder.
Faster Recovery Time Image backups are best known for their quick recovery time allowing users and business to reduce downtime. IT Technicians have known about this major benefit to meeting RTO for years. Recovery Time Objectives (RTO) are built into a business’s disaster protection recovery plan.
The RTO goal is the greatest amount of time that IT systems can be out of order after an unexpected IT crash before negatively impacting operations or profits. The organization analyzes the potential impact that an IT system failure can have upon a business and decides on an RTO goal.
But, unless a business completes a total test restore, predicting the amount of downtime experienced during a complete data recovery process is difficult. Unfortunately, most companies do not complete this crucial task. Therefore, the term “quick” when referring to recoveries is subjective and influenced by multiple variables. Some traditional examples of the variables that may speed or slow a recovery process are 1. the business’s internet speeds and 2. the size of the data set needing to be recovered. However, generally agreed among IT professionals is that the recovery time of an image backup will be far faster and easier compared to using a file and folder backup. It is common for file and folder recoveries to require days spent on data reorganization once the data has been recovered. This downtime will negatively affect RTO goals.
Ease of image backups Performing an image backup recovery restores the data to the PC (or the server) so that the screen appears exactlyas it did the last time the machine was used. The new drive looks identical to the old drive, and it does not require reloading the operating system or reinstalling any programs. This is the way that most people assume data recoveries work. However, complete data recoveries using the file and folder backup methods is a far more time consuming and complex process.
Usually, choosing an individual file or folder from the backup directory using a file and folder backup method is relatively easy. However, performing a complete restoration of data to a computer or server using file and folder backups is notably more difficult than if the user used a(n) image backup/bare metal recovery software.
When is a complete restoration required? A complete restore is frequently required when a user wants to transfer the data from an old computer to a new one. Or when the user has experienced data loss from a crash or cybercrime event. In contrast to an image backup (that magically brings the system back to exactly how it was organized before the crash), a file and folder data backup recovery requires the users to perform multiple steps to recover and reorganize the data to how it appeared before the crash.
The steps to a traditional complete recovery using file and folder data recovery include:
a. Downloading the files and folders stored in the backup copy to the C drive. Most of thefiles and folders will be downloadedto the user’s directory under the downloads directory.
b. The user must then choose files and folders individuallyfrom the C drive to rebuild how the computer screen looked before the crash. Although the directory looksthe same, the PC screen will be a blank canvas that the user needs to recreate. For example, the recovered bookmark links will appear in the download’s directory but will need to be highlighted and dropped and dragged into the proper directory on the PC to function as they did before.
Image backup can also perform file and folder recoveries. Many users new to image backup may not knowthat image backups can also recover files individually.This is the same way a file and folder backup works. This may be a relief to those who are accustomed to file and folder backup methods.
Affordability Supports Greater Access Image backups were late to the game in the backup and recovery industry. A few companies dominated the space, and the image backup software was expensive. Now that the pricing of image backup/bare metal recovery software is comparable with file and folder level costs, most users are switching to an image backup platform. Today, more backup companies have created image backup software. These companies are now competing against each other for business, thus reducing costs and increasing access.
Quick Recovery of Ransomware and Cyberattacks Cybercrime is at an all-timehigh. When a cyberattack restricts the user’s access to their local data, theRemote Data Backups image backup/bare metal recovery restoration process gets the computer running again, free from the initial virus that corrupted the machine with just a few steps.
During this type of disaster, most users would call the www.RemoteDataBackups.com U.S.-based 24/7 tech line at 1-888-722-2587. Remote Data Backups Techs Support guides users through the recovery process with free tech support. Using a USB thumb drive, the user is instructed to download a small file from the Remote Data Backups website. This file allows users to boot up their machine to access the image backup copies stored on their online backup program. The user then chooses a date to roll the image back to before the machine was infected. The image backup then reformats the drive and restores the image to exactly how the PC or server looked before the cyberattack.
In summary, bare metal recovery software/image backup is more relevant today than the file and folder backups of the past thirty-years. And image backup will continue to be the trend. Image backups still retain the granular file and folder recovery capabilities of the past and will remove a large amount of time and frustration from setting up new PCs or completing full system data recoveries.
Learn More: Backup Blog
Why Does SaaS Require 3rd Party Backups?
By Amanda Finch | RDBU Marketing
Common Examples of SaaS Requiring a Third Party Backup:
- Google Drive
- Google Workspace
- Microsoft 365
- File sharing software like Dropbox
- Your CRM (Contact Manager)
The SaaS list above most likely has a built-in backup copy available to you. But surprisingly, it is not reliable. Keep reading to find out why.
What is a third party backup? A third party backup is a backup service company completely unreleated and external from the company that offers the SaaS software that is being used by the client.
What happens if my SaaS account is hacked? Hackers will completely lock down access to your SaaS program, including your access to the only proprietary SaaS backup copy.
What if you need to restore to a previous month, or year? Your SaaS alone cannot perform this task. But a true third party backup can. A company with no ties to your SaaS program, called a third-party backup, ensures that your pc or business server can quickly recover after a data loss.
Fact SaaS (Software as a Service) is not a true backup. Even Microsoft and Google state that if the data is important, users should use a thrid party company for offsite backups.
Microsoft 365 Facts Did you know that safeguarding your Microsoft 365 data requires a thoughtful backup strategy? According to Microsoft’s Shared Responsibility Model, data loss can occur without proper planning, making a third-party backup a wise choice to implement to minimize risks. As a Microsoft 365 user, it’s your responsibility to protect your own data, which is rightfully owned by you. Ignoring this recommendation can lead to a costly, time-consuming, and frustrating situations should data loss occur. However, investing in a true third-party backup solution can provide peace of mind and protection in the event of a Microsoft 365 crash.
Direct Quote From Microsoft of Shared Data Responsibility
“For all cloud deployment types, you own your data and identities. You’re responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control. Cloud components you control vary by service type.
Regardless of the type of deployment, you always retain the following responsibilities:
- Data
- Endpoints
- Account
- Access management (Microsoft direct source: https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility)”.
How It Works And Why Microsoft 365 Is Not A True Backup
A Replicated Version of Data is Not a True Backup: Microsoft 365 hosts a replicated version of your data, but many users are not aware that this replicated version is not a true backup. This replicated copy included with each Microsoft 365 subscription, will contain a dump of all Microsoft 365 data when restored up to 180 days. This data includes data you do may not want or need, data saved previously to recent edits, and data that may have experienced malware or corruption. The user cannot easily pick and choose data versions specific to their needs or timeframe. To further understand how a Microsoft 365 recovery works, visit the official Microsoft 365 recovery page at: https://support.microsoft.com/en-us/office/recover-your-microsoft-365-files-dc901de2-acae-47f2-9175-fb5a91e9b3c8
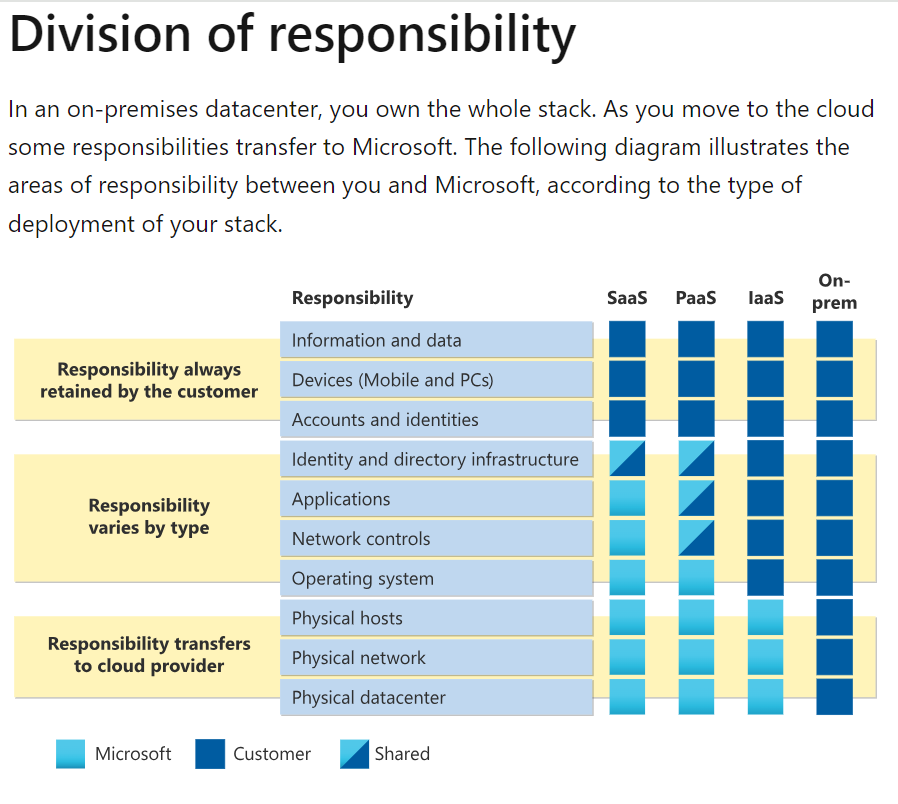
Security Is A Shared Responsibility: Microsoft’s chart, at the bottom of the page, indicates that the user and Microsoft engage in a shared responsibility of protecting data. Microsoft 365 data protection extends to their own Azure onsite data vaults, which protect the user’s settings and offer security through authenticity and ID’s.
In short, Microsoft is the data processor, but the Customer is the responsible Owner of the data. These roles are clarified in Microsoft’s direct statement below:
“As specified by the Product Terms and Microsoft Products and Services Data Protection Addendum (DPA), Microsoft, as a data processor, processes Customer Data to provide Customer the Online Services in accordance with Customer’s documented instructions.cation, and cloud security ID. Beyond this, the data is the customers responsiblity (Source: https://learn.microsoft.com/en-us/compliance/regulatory/gdpr-dpia-office365).”
Next: We discuss further how outside cyberattacks, human error, sabotage, poor digital security management strategy, or the absence of a variety of backup versions are vulnerabilites that can fall outside the reponsibility of the boundaries of Microsoft 365’s repicated copy agreement for data protection. And how these factors can result in costly down-time, potential crisis, and time-consuming data losses.
As a 25-year backup and recovery managed service provider, and recently becoming a Distributor for a suite of data backup products, Remote Data Backups can ensure an external, true, customizable backup of your Microsoft software-as-a-service. A true third-party backup protects your data, eliminating the all-or-nothing data retrieval limitations of the the Microsoft 365 settings replication copy. Remote Data Backups ensures that your company’s settings are configured correctly, and multiple backup versions are available to your business. Our first prioristy is to help our clients to avoid a data and downtime crisis when disaster strikes.
Examples of Microsoft 365 data backup vulnerabilities. Google Workspace experiences similar vulnerabilities:
- Accidental Choosing of the Wrong Data Retention Configurations or Schedules: The settings for retention schedules in Microsoft 365 can be complicated and confusing. Improper configuration can result in an unexpected data loss. However, a third-party backup can turn back the clock to a specific time before the data loss occured, and restore the lost data (even if the customer chose the wrong retention period in Microsoft 365’s settings).
- Human Error or Employee Sabotage: Unfortunately, not all employees can be trusted. Unhappy employees may retaliate by deleting critical data housed within Microsoft 365. By the time the damage is noticed, the retention period for Microsoft 365 backups may have expired. A third-party backup can offer a targeted data retention snapshot as a solution for employee sabotage that corrupted or deleted important datasets.
- Ransomware Attacks or Viruses: Hackers are succeeding today more than ever at stealing information, corrupting, or locking us out of access to our data. And Microsoft 365 is not entirely impervious to attack. Hidden viruses from malware also create disruption. Unforeseen data corruption and cyberattack incidents expose vulnerabilities in the organization that reduce client confidence in your business. A third-party backup can restore your SaaS prior to infection or incident.
- Retention Requirements for Legal Reasons: Some industries mandate up to 7-year retention to ensure compliance with laws. To avoid financial penalties, Choosing a third-party backup provider that can provide the industry retention requirements can help companies to prevent steep fines or legal issues.
- Hybrid Environments for Data Migration or Email: Microsoft 365 is a great program, but configuration can be complicated. To ensure that the data sent using hybrid environments can be stored in the backup set, implementing a third-party backup and recovery provider is a best practice.
- Microsoft Teams Vulnerabilities: Microsoft applications like Teams can be challenging to configure and to ensure a solid backup is happening. Having a third-party backup on board can reduce errors in settings and offer peace of mind that your Team data is being sufficiently protected.
The below chart is directly sourced from Microsoft. It is a visual depiction showing the Customers responsibility, Microsoft responsibility, and the shared resonsibilities of both entities in the various areas of service offered by Microsoft software. Microsoft Direct Source Link: https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
Learn More: Backup Blog
Why Software as a Service (SaaS) Requires a Separate Backup
By Amanda Finch | RDBU Marketing
Quick Facts
- Software as a Service (SaaS) data like Microsoft 365, Google Workspaces, Dropbox, or your CRM requires a specific type of backup called SaaS backup.
- These companies advise users use a third-party backup.
- Image and file and folder backup do not protect SaaS data.
- SaaS is extremely vulnerable to cyberattacks.
Isn’t my SaaS data already protected? The simple answer to that question is mostly no, and somewhat yes. Modern users depend on SaaS programs for day-to-day operations. And today’s computers and software are more complicated than in the past. Microsoft Office data used to be synced and stored locally for common products like Microsoft Word, Microsoft Excell, Microsoft PowerPoint and Microsoft Outlook. Microsoft’s 365 version now promotes their own OneDrive cloud storage backup. SaaS data is stored automatically to the Microsoft’s OneDrive cloud by default. Microsoft 365 does offer users an option for local storage. Google Workspaces is another popular SaaS that uses proprietary storage.
But, it is a wide-spread misconception that SaaS data stored in these proprietary clouds is protected. In fact, included in the terms and conditions shared responsibility section for both of these companies is the recommendation that users install an additional backup program unaffiliated with their company.
Big mistakes can be prevented by choosing an unaffiliated backup and recovery company. And SaaS backups are now affordable. Because the devil is in the details, even tech-savvy companies sometimes have had to learn the hard way when it comes to a SaaS related data loss.
Why are retention windows so important? Google Workspace G Suite has 30-60 days of retention to recover data sets from. And Microsoft 365 stores 14-days of data. These windows are short. A third-party SaaS backup like Remote Data Backups Datto Backup has a one-year, 7-year, or infinite choice of retention. Many companies are required by their Industry to store data for certain lengths of time to maintain Industry compliance.
What happens when SaaS files won’t open? As a personal example, some of my personal older Google Workspace pdf. documents could not be opened. And this is not uncommon. Over the years, this problem has been reported by many users. Perhaps there are workarounds to open these documents. However, troubleshooting will most likely be a time-consuming and research-intensive process, also requiring updates. A third-party SaaS backup can roll back the clock to a version of the document before an upgrade or corruption occurred which stopped the document from being able to be accessed.
Can I get technical support with my SaaS backup? Technical support for the backup and recovery software through most SaaS companies is limited. A third-party SaaS backup, like Remote Data Backups, offers included 24/7 support by understandable US-based techs. And there are no additional fees for escalated technical support services.
Remote Data Backups is a 25-year Backup and Recovery Distributor with 24/7 U.S.-based support. Our affiliate program is 25 years strong. Partners receive an onboarding affiliate link to post within their content. This link allows RDBU affiliates to receive credit for new clients automatically. Our partners receive a 20% recurring income month after month. RDBU manages all clients and tech support. Reoccurring affiliate commission checks are directly deposited monthly. Backup and Recovery is our niche and area of expertise, and our partners built our business. Our service supports backups for PC’s, servers, SaaS, and virtual machines
Human Support
1 (866) 722-2587
Support Hours 24/7
Get Started
Let us answer your questions. Call now to speak to an expert or book an appointment today. Consultations are always free
Datto Distributor
Kaseya 365 Distributor
Trust The Lighthouse
A solution for every backup & recovery need.
Human Support
1 866 722 2587
TOOLS
Gartner Reviews:


